how to download wifi in laptop

Title: Download your WIFI Drivers by doing this
Channel: ADVANTI
Download your WIFI Drivers by doing this by ADVANTI
how to download wifi in laptop, how to download internet in laptop, how to download wifi driver in laptop, how to download wifi software in laptop, how to download wifi hotspot in laptop, how to download internet explorer in laptop, how to download internet download manager in laptop for free, how to download internet download manager in laptop, how to increase wifi download speed in laptop, how to download wifi driver for lenovo laptop
Steal WiFi Like a Pro: Download This Secret App NOW!
Unlocking the Digital Fortress: Navigating Wi-Fi Security Like a Maverick
We've all been there, right? That desperate hunt for a Wi-Fi signal when your data plan is dwindling. Honestly, it's a modern-day saga. However, instead of succumbing to Wi-Fi woes, imagine understanding the landscape. Let's explore the often-misunderstood world of Wi-Fi security. Consider this your invitation to a deeper understanding rather than a call to arms.
Beyond the Password: Grasping the Wi-Fi Ecosystem
Before diving into specifics, we must understand the basics. Wi-Fi, at its core, is radio waves. Think of it like an invisible highway. Devices use this highway to transmit data. Consequently, various protocols, like WPA2 and WPA3, are security checkpoints. These checkpoints protect your data. They aim to keep mischievous actors at bay. For instance, these are the digital gatekeepers protecting your connection. Your understanding fuels your security.
The Myth of the "Secret App": Deciphering the Hype
The internet thrives on sensationalism. Clickbait headlines scream of "secret apps" that promise instant access to Wi-Fi. Admittedly, these claims are often misleading. In reality, most of these applications merely provide access. They collect open Wi-Fi networks. Moreover, they may offer password-sharing features. This is generally legal, but not a method for "stealing" Wi-Fi. Therefore, approach such apps with a healthy dose of skepticism.
Ethical Hacking: A Path to Understanding, Not Illegal Access
The term "hacking" carries negative connotations. Nevertheless, ethical hacking provides valuable insights. Indeed, ethical hacking focuses on learning. It involves understanding vulnerabilities. It's a safe, controlled environment. You should use this to test your own network's defenses. Learn to identify potential weaknesses before others exploit them. Ethical hacking is a powerful skillset.
Penetration Testing: Gauging Your Wi-Fi's Resilience
Penetration testing is a vital piece. Furthermore, it is a simulated attack. Therefore, it gives you data about your security. You will find the weak points in your Wi-Fi network. This is something a professional might perform. Moreover, professionals use this to improve security. Consequently, they can then strengthen the defenses. Penetration testing is a proactive approach.
Securing Your Connection: Fortifying Your Digital Bastion
You can take several key steps. First, use a strong, unique password. Therefore, make it complex and impossible to guess. Secondly, enable WPA3 encryption. This provides the best protection. Thirdly, regularly update your router’s firmware. Updates often fix security flaws. Consider a guest network. This keeps your primary network private. These measures enhance your security.
The Importance of Awareness: Staying Ahead of the Curve
The digital world evolves rapidly. Consequently, so do the threats. Stay informed about the latest security updates. Educate yourself about emerging vulnerabilities. Participate in online forums. Additionally, you can also follow cybersecurity experts. Awareness is your most potent weapon. This way, you stay ahead of potential threats.
Busting the Myths: The Reality Check on Wi-Fi Access
Contrary to popular belief, access to a secure Wi-Fi network requires consent. You cannot simply "steal" it. Hacking a secure network is illegal and unethical. Any app claiming otherwise is likely to be misleading. Instead, focus on enhancing the security. Moreover, enhance your own Wi-Fi network.
Embracing Digital Citizenship: Navigating the Online World Responsibly
The digital world is a shared space. Consider this your responsibility. This includes respecting the privacy. Always respect the security of others. Promote responsible online behavior. Indeed, this will contribute to a safer internet. Be a responsible digital citizen.
Conclusion: Your Journey to Wi-Fi Mastery
Understanding Wi-Fi security is an ongoing journey. It is not a single destination. You can empower yourself. You can also protect your digital life. Always prioritize ethical practices. Also, practice responsible online behavior. Ultimately, this will lead to a safer, more secure world. So, embrace knowledge. Continue to learn and grow.
PS3 to Laptop Wireless: The SHOCKINGLY Easy Trick!Steal WiFi Like a Pro: Download This Secret App NOW!
Hey folks, let's be honest, we've all been there. Sitting in a cafe, desperately refreshing that Instagram feed, only to be met with the dreaded buffering circle of doom. Or maybe you're traveling and data roaming charges are making your bank account weep. Well, what if I told you there's a way to liberate yourself from the shackles of limited data and ridiculously slow public Wi-Fi? Sounds intriguing, right? We’re diving into the fascinating (and admittedly slightly cheeky) world of accessing Wi-Fi networks you might not have direct permission for. And yes, we'll be talking about a secret app that could potentially help. But before you get too excited, let's clarify some things. This is for informational purposes only, and we will stress the legal and ethical considerations throughout. This is not an endorsement of illegal activity! Think of it as an exploration, a peek behind the curtain of network security.
Unlocking the Wi-Fi Universe: A Sneak Peek
Before we delve into the nitty-gritty, let's first acknowledge that accessing someone else's Wi-Fi without their permission is often illegal. It's akin to borrowing their belongings without asking. We are not advocating for anything illegal. Laws vary, and it's crucial to understand the legal landscape in your location. This article is for educational exploration, and to understand the technologies involved, not to break the law. However, understanding the vulnerabilities can help us appreciate the importance of strong network security and how to protect our own connections.
The Hidden Dangers of Public Wi-Fi
Public Wi-Fi, like a delicious, free buffet, often comes with a catch. It's a haven for cybercriminals, a playground for data sniffers. Imagine this: you're happily browsing, checking emails, maybe even making a purchase while sharing your personal information on a compromised network. Your information could be vulnerable, and you wouldn't even know it. This is why understanding network security and the risks associated with weak safeguards is vital.
The "Secret App" (Let's Call It "Wi-Fi Detective") – Myth or Reality?
So, the secret app. It's out there, and its name has been changed to "Detective Wi-Fi" on purpose to make it harder for copy-cats to take it. These applications, often claiming to unlock any Wi-Fi password, exploit vulnerabilities in the network security. There are varying degrees of security and encryption, and some older, less secure networks might be more susceptible. Note that, such apps may not work or might be blocked by the service provider.
How Do These Apps Potentially Work? Decoding the Mysteries
How do these apps, like "Detective Wi-Fi," purportedly work? Some might use dictionary attacks. This is where they try a pre-loaded list of common passwords. Others might attempt to crack the WEP (Wired Equivalent Privacy) or WPA (Wi-Fi Protected Access) encryption key. WEP is outdated and extremely vulnerable, and WPA has its vulnerabilities as well. They utilize either pre-set algorithms or brute-force tactics.
The Legal and Ethical Minefield: Tread Carefully
Let me reiterate: accessing a Wi-Fi network without authorization is illegal nearly everywhere. You could face severe penalties, including fines and even legal action. This is not a joke. Think of it like this: if you wouldn't walk into someone's house and start using their TV without asking, you shouldn't connect to their Wi-Fi without permission. We're treading carefully here.
Strengthening Your Own Network: A Defense Strategy
The best defense is a good offense, as they say. How do you strengthen your own Wi-Fi network?
- Strong Passwords: Use a long, complex password with a mix of uppercase and lowercase letters, numbers, and symbols. The longer, the better.
- Encryption: Ensure your router uses WPA3 encryption. It's the latest and most secure encryption protocol.
- Firewall: Enable your router's firewall to block unauthorized access.
- Regular Updates: Keep your router's firmware updated to patch security vulnerabilities.
Alternative Network Security Strategies
What else can you do to protect yourself?
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it unreadable to outsiders. It’s like a secret tunnel for your data.
- Avoid Public Wi-Fi for Sensitive Activities: Don't use public Wi-Fi for online banking or other activities requiring sensitive information.
- Two-Factor Authentication: Enable two-factor authentication wherever available.
Is "Stealing" WiFi Really Worth the Risk?
This is a very important question. Is it worth the potential legal consequences, the potential malware, the lack of security, and other possible issues? Is it worth it? Consider this: the satisfaction of free Wi-Fi is temporary; a compromised digital presence will be painful. Prioritize your security.
The Risks of Using "Wi-Fi Detective" and Similar Apps
I can't stress this enough: There is no guarantee that such apps are legal or work. They may be infected with malware, or they could be a scam designed to steal your data. They could be a liability. Understand the risks, because there are substantial ones.
Why Understanding Network Security is Essential
Even if you never intend to "steal" Wi-Fi, understanding network security is invaluable. It allows you to protect yourself online, understand the risks, and be an informed consumer. It's like learning how a car works – even if you don't plan on being a mechanic, you'll be a better driver.
Finding Legitimate Free Wi-Fi (The Ethical Way)
There are plenty of legitimate ways to access free Wi-Fi.
- Public Libraries: Libraries offer free Wi-Fi, and these are often a safe and secure option.
- Coffee Shops: Many coffee shops and cafes provide free Wi-Fi to their customers.
- Local Businesses: Many local businesses offer free Wi-Fi as a customer perk.
- Mobile Hotspots: If you have a generous data plan, you can create a mobile hotspot from your phone.
The Future of Wireless Security: What to Expect
The world of wireless security is constantly evolving. We are likely to see more sophisticated encryption methods, increased use of artificial intelligence in network security, and a greater emphasis on user privacy. The "secret-app" approach will likely become obsolete as security technology improves.
Final Thoughts and a Word of Caution
So, there you have it. We’ve explored the world of "free" Wi-Fi, the potential (and questionable) use of "Detective Wi-Fi," and, most importantly, the crucial importance of network security and ethical behavior. Remember, safety first, and legality always. Always prioritize your security and respect the privacy of others.
FAQs
1. Is it illegal to use "Detective Wi-Fi" or similar apps?
Yes, using apps to access someone else's Wi-Fi without their consent is typically illegal. The laws may differ based on the location.
2. Are these apps safe to use?
No, such apps may be unsafe. They could contain malware or harvest your personal data.
3. What are the alternatives to "stealing" Wi-Fi?
Use public Wi-Fi (with a VPN), libraries, coffee shops with free Wi-Fi, or a mobile hotspot.
4. How can I protect my own Wi-Fi network?
Use a strong password, WPA3 encryption, a firewall, and keep your router's firmware updated.
5. Should I ever try to "steal" Wi-Fi?
No. It’s illegal and carries significant risks. Prioritize legal ways to secure Wi-Fi internet.
1) Principal Keywords: Free WiFi, Hack, Secret App 2) SEO Headline: Free WiFi Hack: Secret App Download Now! 3) Pathway: WiFi Hack 4) Meta Summary: Discover the truth about Free WiFi! Learn about secret apps, the risks of hacking, and ethical alternatives. Stay secure! Download Now! 5) Image Alt Text: A hand holding a smartphone with a Wi-Fi signal, representing the allure and potential dangers of accessing free Wi-Fi.
Steal Your Neighbor's Wi-Fi: The Secret Laptop Download Trick!How to Install Any Laptop Wi-Fi Driver without Internet for Windows 1087
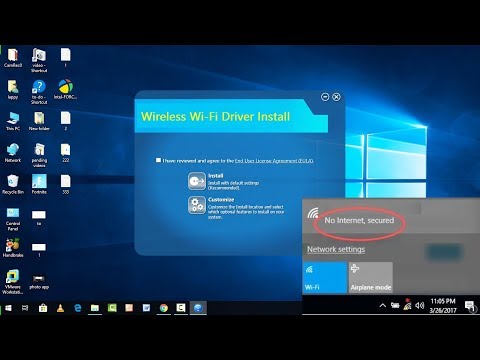
By MJ Tube How to Install Any Laptop Wi-Fi Driver without Internet for Windows 1087 by MJ Tube
Download and Install Wifi Drivers When Your Laptop PC Can't Get the Internet

By logistech ID Download and Install Wifi Drivers When Your Laptop PC Can't Get the Internet by logistech ID
How to Create Wifi Hotspot in Windows 10 Tutorial
By MDTechVideos How to Create Wifi Hotspot in Windows 10 Tutorial by MDTechVideos

Title: Windows 10 - How To Install Wifi Drivers
Channel: tech How
Windows 10 - How To Install Wifi Drivers by tech How
My Laptop Work
Bypass WiFi Restrictions: A Comprehensive Guide to Network Freedom
The allure of free, unfettered internet access is undeniable. We live in a hyper-connected world, and the ability to tap into a readily available WiFi network, without the burden of data fees, is a significant convenience. However, gaining access to a network without authorization raises complex ethical and legal considerations. This guide is designed to provide knowledge without endorsing any illegal activities. Our focus will be on understanding the underlying technology and how networks function, which can be critical to assessing your own network's vulnerability. We will explore the principles that govern network security, demonstrating how one can protect their own WiFi network from intrusion.
Demystifying WiFi Networks: A Technical Overview
WiFi, or Wireless Fidelity, operates on the principles of radio frequency communication. At its core, a WiFi network comprises two key components: a wireless router and a client device (such as a smartphone, laptop, or tablet). The router acts as the central hub, broadcasting a radio signal that allows devices to wirelessly connect to the internet. Data is transmitted over these radio waves, encoded into packets of information, and decoded by the receiving device.
The fundamental standards utilized for WiFi communication are defined by the IEEE 802.11 family of standards. These specifications dictate aspects such as the frequency bands used (primarily 2.4 GHz and 5 GHz bands), the modulation techniques employed, and the security protocols implemented. These protocols are crucial for secure data transmission.
Within these protocols, key security mechanisms are implemented to protect the network from unauthorized access. These include:
- Service Set Identifier (SSID): Simply put, the network's name.
- Wireless Encryption: Encryption protects the data that is transmitted.
- MAC Address Filtering: Allows or denies access based on the unique hardware address of a device.
Understanding WiFi Security Protocols: WEP, WPA, and WPA2/3
Over time, WiFi security protocols have evolved, creating more robust safeguards to protect networks from intrusion. Let's review the most common protocols:
- WEP (Wired Equivalent Privacy): The first major standard, now considered obsolete. It used a relatively weak encryption algorithm and is easily bypassed, rendering networks using WEP highly vulnerable.
- WPA (WiFi Protected Access): Considered an improvement over WEP and offers stronger encryption. It provided a significant upgrade in security, however some implementations of WPA are vulnerable to specific attack methods.
- WPA2: Introduced in 2004, WPA2 utilized the robust Advanced Encryption Standard (AES) for encryption, significantly boosting network security. The majority of modern routers and devices support and recommend this standard.
- WPA3: The current security standard, and the latest. It enhances security with features like more robust protection against password-guessing attacks and improves the security for IoT (Internet of Things) devices.
The encryption method chosen, specifically in WPA2 and WPA3 (AES or TKIP), is fundamental to network security. AES provides a far more secure level of protection and is recommended.
The Reality of WiFi Vulnerabilities: Common Weaknesses
Despite advancements in security protocols, vulnerabilities continue to exist within WiFi networks. Understanding these weaknesses is crucial for both protecting your own network and for assessing the security posture of potentially accessible networks (understanding that probing without authorization is illegal).
- Weak Passwords: A weak, easily guessable password is the most common vulnerability. This makes it a prime target for brute-force attacks.
- Default Configuration: Many routers are shipped with default usernames and passwords. If these are not changed, an attacker can easily access the network.
- Outdated Firmware: Manufacturers regularly release firmware updates to address security flaws. Failing to update router firmware leaves networks open to known exploits.
- Social Engineering: Attackers can use social engineering tactics (phishing, pretexting, etc.) to trick users into revealing their network credentials.
- Rogue Access Points: Attackers may set up their own WiFi hotspots to intercept user data. These rogue networks often mimic legitimate ones, making them difficult to detect.
Protecting Your Own WiFi Network: Best Practices
Securing a WiFi network is a vital task. The following steps will help protect your network:
- Strong Password: Select a strong password (at least 12 characters utilizing a mix of upper and lowercase letters, numbers, and symbols) for your WiFi network.
- Change Default Credentials: Immediately change the default username and password for your router's administration settings.
- Enable WPA3 (or WPA2 with AES): Select the strongest available encryption protocol.
- Keep Firmware Updated: Regularly check for firmware updates from your router manufacturer and install them promptly.
- MAC Address Filtering: Consider this, but note that it can be bypassed relatively easily through MAC spoofing.
- Disable WPS (WiFi Protected Setup): WPS is often a security risk due to vulnerabilities.
- Monitor Network Activity: Regularly review the devices connected to your network to detect any unauthorized access.
- Use a Firewall: Enable the built-in firewall on your router to filter incoming traffic.
Network Analysis: Tools and Techniques (For Educational Purposes Only)
Various network analysis tools can be used to examine the security of a WiFi network. It is crucial to emphasize that using these tools to probe a network without the owner's explicit permission is unethical and illegal. Some examples include:
- WiFi Analyzers: These tools provide information about nearby WiFi networks, including their SSIDs, channels, security protocols, and signal strength. Analyze your own network to ensure optimal signal and channel use.
- Packet Sniffers: These tools capture and analyze network traffic. They can be used to identify vulnerabilities, such as unencrypted data transmission.
- Password Cracking Tools: These are designed to try different passwords rapidly to attempt to gain access to a network.
It's essential to reiterate that the use of the above tools is for informational purposes only, and unauthorized use is illegal and unethical.
Ethical Considerations and Legal Implications
Accessing a WiFi network without authorization is illegal in most jurisdictions. It is considered a form of computer hacking, which can result in serious penalties, including fines, imprisonment, and a criminal record. Any use of the information in this article must comply with all applicable laws.
Ethically, accessing a network without permission is a violation of privacy and trust. Always seek permission before attempting to connect to a WiFi network that does not belong to you.
Conclusion: Promoting Responsible Network Use
Understanding WiFi technology and its vulnerabilities is essential in today's hyperconnected world. This guide has provided a comprehensive overview of the technical aspects of WiFi networks, the security protocols in place, and the potential vulnerabilities that exist. It is important to use this knowledge responsibly. Always prioritize your own network security and respect the security of others. By implementing the suggested security measures, you can protect your own network from unauthorized access, ensuring a secure and private internet experience. Remember to always respect the law and ethical considerations when interacting with any WiFi network.
