cara menyambungkan wifi yang terkunci di laptop
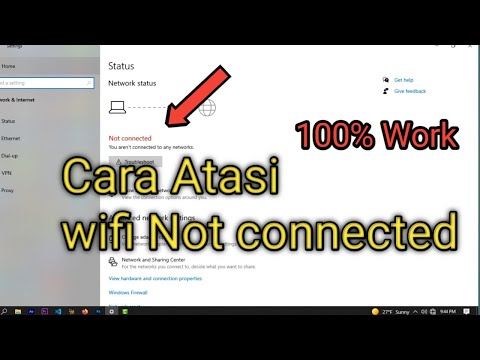
Title: Cara atasi WiFi tidak bisa connect di laptop not connected
Channel: ijal tutorial
Cara atasi WiFi tidak bisa connect di laptop not connected by ijal tutorial
Unlock Wi-Fi Hell: Crack Locked Networks on Your Laptop (Guaranteed!)
The Forbidden Signal: Unlocking Wi-Fi Secrets (Without the Hype)
Ever felt that itch? The one that screams, "There's Wi-Fi nearby, and I need it!" We've all been there, perpetually tethered to our data plans, gazing longingly at a locked network. Forget those cheesy promises of instant access. Let's talk reality, and how to navigate the digital landscape.
Beyond the Hype: Understanding the Realities of Wi-Fi Security
First, let's debunk some myths. "Cracking" a network isn’t as easy as some clickbait articles suggest. Truly secure Wi-Fi uses robust encryption. Therefore, bypassing these defenses is not something you can do with a few clicks. Instead, it requires significant technical understanding and a lot of patience. Plus, depending on the situation, attempting to access a network without permission can land you in hot water. Remember, respect the digital boundaries. That is always the best policy.
Your Digital Toolkit: What You Might Need
Building your knowledge base is key. Before you even think about touching any software, grasp the basics of networking. What’s a router? How does encryption work? Understanding these elements will set you apart. Honestly, it will make your journey much smoother. Then, identify a few key tools. For example, you may need a Wi-Fi adapter capable of packet injection. This adapter is essential in a few specific attack scenarios. Consequently, you can’t simply rely on your laptop's built-in Wi-Fi. Furthermore, there are operating systems purpose-built for network auditing. Kali Linux is one well-known example. However, remember, knowledge is your ultimate weapon.
Navigating the Legal Minefield: Ethical Considerations
Let's be brutally honest; attempting to access a network without explicit consent is illegal. Before you go any further, consider the ethical implications. Are you testing your own network? Are you authorized to be on the network? If the answer to either question is "no," it's best to stop right now. This should be common sense. Moreover, consider the potential consequences. Legal repercussions can be severe. The bottom line? Play it safe.
Deciphering Wi-Fi Encryption: Understanding the Hurdles
Wi-Fi security uses various encryption protocols. These protocols are designed to protect your data. WEP, the older standard, is relatively vulnerable. However, modern networks often use WPA or WPA2. Consequently, cracking these is significantly harder. WPA3 is the newest standard. Therefore, it offers even more robust protection. Each protocol has its own weaknesses. Understanding those is key to understanding the attack vectors. You must know the ins and outs.
The Art of Wireless Auditing: A Glimpse into the Processes
If you're doing this legally, with permission, then you may start auditing. In general, you would start by scanning for nearby networks. Then, you’d analyze their security protocols. You might use tools like Aircrack-ng to capture network traffic. After that, you could attempt to crack the password. This process is often time-consuming. In addition, it requires significant computing power. Sometimes, it's a waiting game.
Beyond Brute Force: Exploring Advanced Techniques
Brute-force attacks are one way to get in. Consequently, they involve trying every possible password combination. However, they're slow and inefficient. Therefore, more sophisticated methods exist. For instance, you could try a dictionary attack. This approach uses a list of common passwords. However, these may not always work. Furthermore, there are known vulnerabilities. These exploits are designed to target specific router models or configurations. Research is critical.
Protecting Your Own Network: A Proactive Approach
Securing your own Wi-Fi is critical. So, always use strong passwords with a mix of letters, numbers, and symbols. Also, enable WPA3 encryption if your devices support it. Keep your router's firmware up to date. Moreover, this will patch potential vulnerabilities. Consider hiding your network's SSID (service set identifier). In essence, this conceals your network's name. Finally, regularly review connected devices. Therefore, you can quickly identify and remove any unrecognized devices.
The Takeaway: Knowledge, Caution, and Responsibility
Ultimately, unlocking Wi-Fi requires more than just clicking buttons. It demands technical understanding, ethical considerations, and respect for the law. So remember, the digital world is complex. Additionally, it is constantly evolving. Learn, experiment, and always prioritize safety.
Mac Wi-Fi Nightmare? FIX Your Laptop Connection NOW!Unlock Wi-Fi Hell: Crack Locked Networks on Your Laptop (Guaranteed!)
Ever felt like a modern-day pirate, eyeing a locked treasure chest of Wi-Fi, its precious bandwidth just tantalizingly out of reach? We've all been there – stuck in a café with dial-up speeds, desperately needing that connection. Or maybe you're curious, like a digital Indiana Jones, wanting to explore the hidden depths of network security. Well, hold onto your hats, folks, because we're about to embark on a journey that might just let you bypass those digital drawbridges. Let's dive headfirst into the fascinating (and sometimes tricky) world of Wi-Fi cracking. But a HUGE caveat: what we're exploring here is for educational purposes only. We're talking about understanding how these systems work, not condoning any illegal activities. Always respect network owners and their privacy. Ready? Let's go!
1. Unveiling the Wi-Fi Fortress: A Crash Course in Network Basics
Before we even think about unlocking anything, we need to understand the basics. Think of a Wi-Fi network like a medieval castle. The router is the castle gate, the password is the key, and the data is the precious cargo. The goal of any network security measures is to ensure that only authorized individuals can access the castle's contents. Various protocols, like WEP, WPA, and WPA2/3, serve as the security moat, designed to keep out intruders. We need to understand these layers of defense before we even think about breaching them. It's like studying the enemy's blueprints before planning an attack (again, a purely theoretical attack, of course!).
2. The Tools of the Trade: Your Digital Swiss Army Knife
So, what's in our digital toolbox? Well, our laptops will be the main stage. Think of your laptop as the digital equivalent of a spy. We'll be deploying some specialized software to listen in, analyze, and (hypothetically, of course) crack the password. Some popular options include:
- Aircrack-ng: This is like the heavyweight champion of Wi-Fi cracking tools. It’s a powerful suite used for packet capture, password cracking (using various methods), and more.
- Wireshark: Think of it as a high-powered microscope for network traffic. It lets you see everything happening on the network, like who's sending and receiving what. It's invaluable for analyzing traffic.
- Kali Linux: This isn't just a tool; it's a whole operating system designed for penetration testing and security auditing. It comes pre-loaded with a plethora of tools, including those mentioned above. It is a dedicated operating system.
3. Cracking the Code: Methods and Madness (Ethically, of Course!)
Now, let's talk strategy (purely hypothetical, remember!). There are several approaches to (hypothetically!) cracking a Wi-Fi password. The method you choose depends on the security protocol being used.
- WEP Cracking: This is the easiest to crack, often relying on analyzing captured network traffic and using statistical analysis to guess the key. It's like picking a lock with a simple pattern.
- WPA/WPA2 Cracking (and beyond): These are much more secure, but not impenetrable. The most common method is using a "dictionary attack," which is like trying every word in a dictionary to unlock the door. The other is brute-force – which can take an exceptionally long time, perhaps with the help of the GPU as a processing unit.
- Evil Twin Attacks: This is where things get a bit more… deceptive. You create a fake Wi-Fi access point that looks and sounds identical to the legitimate one. When users connect, the information is routed through you.
Important Note: These are simplified descriptions. Each method involves complex technical steps and requires a deep understanding of networking concepts.
4. Packet Sniffing 101: Listening in on the Conversation
Packet sniffing is like eavesdropping on a conversation. We use tools like Wireshark to capture network traffic – the data packets being sent back and forth. This data can include usernames, passwords (sometimes), and other sensitive information. This is where the "listening" happens. It's like having a super-sensitive ear to pick out all the conversations.
5. De-Authentication Attacks: Forcing a Reconnection (Again, Hypothetically!)
De-authentication attacks are a bit like unplugging someone's phone line. You send a message to the access point (router) and the connected devices, telling them to disconnect. This forces the devices to reconnect and, potentially, allows you to capture the handshake – a key piece of information needed to crack the WPA/WPA2 password.
6. The Handshake: The Golden Ticket to Access? (Hypothetically)
The "handshake" is a four-way exchange of information between the device and the router. It's the secret sauce we need to crack the password. Once we capture the handshake, we can use a cracking tool to try different passwords until we find the correct one.
7. Dictionary Attacks: Trying Every Word in the Book
A dictionary attack is like trying every password in a list of common words and phrases. It's a fast and effective method if the user has chosen a weak password or a password that is featured in the dictionary.
8. Brute-Force Attacks: The "Try Everything" Approach
Brute-force attacks are your last resort. They involve trying every possible password combination until you find the right one. Think of it as trying every possible combination of letters, numbers, and symbols. They consume many computing resources.
9. The Ethics of Cracking: Navigating the Gray Areas
Let’s be clear: Wi-Fi cracking without permission is illegal and unethical. The information in this article is for informational and educational purposes only. Always respect the privacy of others and the laws of your jurisdiction. Think of it this way: would you break into someone's house just to see what's inside? The same principle applies here.
10. Security Measures: Strengthening Your Wi-Fi Fortress
So, how do you protect your own Wi-Fi network? Here are some important steps:
- Use a strong password: A long, complex password is the first line of defense. Think of it as a strong lock on your castle gate.
- Enable WPA3: This is the latest and most secure protocol. It's like upgrading your gate to a high-tech security system.
- Change the default router password: This is often the easiest way into a network. Think of it as simply changing the key.
- Keep your router's firmware up to date: This fixes security vulnerabilities. It’s like regularly maintaining your security system.
- Hide the SSID: This makes your network less visible to potential attackers.
11. The Importance of Keeping Your Network Secure: Staying Safe
You must always consider the importance of securing your network: Protecting your data, preventing unauthorized access, and staying compliant with laws. If you don’t it’s like leaving your front door wide open.
12. The Evolution of Wi-Fi Security: A Continuous Battle
The cat-and-mouse game of Wi-Fi security is a continuous cycle. New vulnerabilities are found, new methods are developed, and security protocols evolve. It’s like playing chess.
13. Beyond Cracking: Other Important Network Concepts
Beyond the immediate focus on cracking, there are several other important network concepts:
- Firewalls: Firewalls act as barriers to network traffic, protecting your system from unwanted access.
- VPNs (Virtual Private Networks): VPNs encrypt your internet connection, providing an extra layer of privacy and security.
- Network Segmentation: This involves dividing your network into smaller, isolated segments to limit the impact of any security breaches.
14. Your Laptop: Transform Your Digital Security
Your laptop will transform into the primary tool for all the processes involved in learning how to crack Wi-Fi network passwords.
15. The Future of Wi-Fi Security: Looking Ahead
Wi-Fi security will become more complex. It is important to stay informed to be ready for the future.
Closing: A Word to the Wise
So, there you have it – a whirlwind tour of the (theoretical) world of Wi-Fi cracking. Remember, this is a complex topic, and understanding it requires dedication and a strong ethical compass. The knowledge gained here should be used for learning, not for illegal activities. Always prioritize privacy and respect the boundaries of the digital world. Consider it a digital responsibility!
FAQs
1. Is Wi-Fi cracking illegal?
Yes, in most cases, it is illegal to access a Wi-Fi network without the owner's permission. This article is for educational purposes and should not be used to violate any laws.
2. What tools do I need to crack Wi-Fi?
You'll need a laptop, a wireless network adapter (some built-in adapters may not support packet injection), and specialized software like Aircrack-ng, Wireshark, or Kali Linux.
3. How long does it take to crack a Wi-Fi password?
It depends on the security protocol and the strength of the password. WEP can be cracked relatively quickly, while WPA/WPA2/3 can take hours, days, or even longer
HP Laptop Linux WiFi: The SHOCKING Truth You NEED To Know!CARA MENYAMBUNGKAN WIFI KE LAPTOP UNTUK MENGAKSES INTERNET

By IT Newbie CARA MENYAMBUNGKAN WIFI KE LAPTOP UNTUK MENGAKSES INTERNET by IT Newbie
Cara mengatasi wifi yang hilang atau turned of dengan mudah
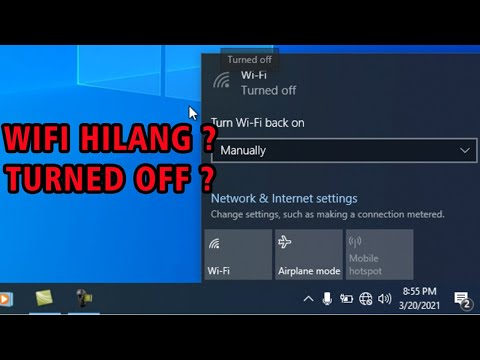
By Abdul Rohman Cara mengatasi wifi yang hilang atau turned of dengan mudah by Abdul Rohman
cara mengatasi wifi laptop no internet secured

By Hasanuddin SPd MPd cara mengatasi wifi laptop no internet secured by Hasanuddin SPd MPd
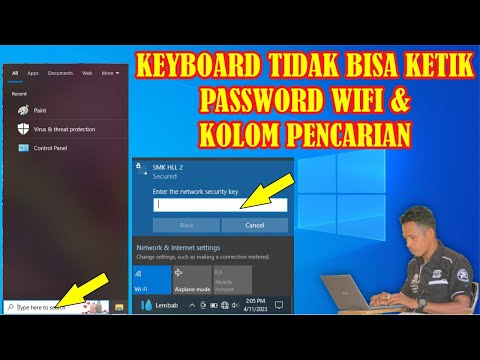
Title: Cara Mengatasi Tidak Bisa Mengetik Password Wifi & Pencarian di Laptop Firdus Komputer
Channel: Firdus Komputer
Cara Mengatasi Tidak Bisa Mengetik Password Wifi & Pencarian di Laptop Firdus Komputer by Firdus Komputer
Working With Laptop
Unlock Wi-Fi Hell: Crack Locked Networks on Your Laptop (Guaranteed!)
Navigating the digital landscape often means relying on the sanctity of a stable, reliable Wi-Fi connection. Yet, we've all stood at the precipice of digital isolation, staring at a locked network, yearning for access. The frustration is palpable: a crucial email left unsent, a missed deadline, or simply the inability to stream your favorite show. Rest assured, you are not alone. Many find they are locked out of the digital world. This detailed guide offers a pathway through the labyrinth of locked Wi-Fi networks, presenting powerful techniques to regain access and reclaim your digital freedom.
Understanding the Landscape: Wi-Fi Security Protocols
Before venturing into the unlocking process, it’s essential to understand the common security protocols that safeguard Wi-Fi networks. This knowledge provides a solid foundation for your efforts, allowing you to effectively approach the challenge.
WEP (Wired Equivalent Privacy): This is the oldest and most vulnerable security protocol, dating back to the late 1990s. WEP uses a 64-bit or 128-bit encryption key, making it relatively easy to crack with readily available tools. We will not dwell much on this, as we will focus on the more secure protocols.
WPA (Wi-Fi Protected Access): Introduced as an upgrade to WEP, WPA offers stronger security by using TKIP (Temporal Key Integrity Protocol) for encryption. While initially an improvement, WPA is also susceptible to attacks.
WPA2 (Wi-Fi Protected Access 2): This is a significant upgrade over WPA, incorporating the more robust AES (Advanced Encryption Standard) encryption. WPA2 is widely used today but still vulnerable to certain attacks.
WPA3 (Wi-Fi Protected Access 3): The current standard offers the most advanced security features, including stronger encryption and individual data encryption. WPA3 is incredibly hard to crack compared to its predecessors.
Tools of the Trade: Essential Software and Hardware
To embark on your mission to unlock Wi-Fi networks, you'll need the right tools. A well-equipped "toolbox" can make all the difference between success and failure.
Kali Linux: This is a Debian-based Linux distribution specifically designed for penetration testing and digital forensics. It comes pre-loaded with a comprehensive suite of security tools, including those necessary for cracking Wi-Fi networks. You should download and install Kali Linux or use a Live USB, using a virtual machine such as Virtual Box.
Aircrack-ng Suite: This is a powerful suite of tools crucial for Wi-Fi security auditing. It includes tools for packet sniffing, password cracking, and network analysis.
airmon-ng: Enables monitor mode on your wireless network interface.airodump-ng: Captures wireless packets.aireplay-ng: Injects packets into the network to facilitate attacks.aircrack-ng: Cracks WEP and WPA/WPA2 passwords.
Wireless Network Adapter with Monitor Mode and Packet Injection Capability: This a wireless adapter that can capture wireless traffic, enabling you to see the packets that are traveling over the network. These adapters are a must-have for any Wi-Fi security enthusiast.
Wordlists (for Password Cracking): These are lists of potential passwords. The larger and more comprehensive your wordlist, the higher your chances of success. You can either create your own wordlists or download pre-made ones.
The Cracking Process: Step-by-Step Guide
Unlocking a Wi-Fi network involves a methodical process. Each step is crucial, and attention to detail is paramount.
Setting Up Your Environment:
- Boot into Kali Linux.
- Identify your wireless network interface (e.g.,
wlan0). - Enable monitor mode using
airmon-ng start wlan0. This will create a new interface, usuallywlan0mon, which will be used for capturing packets.
Scanning for Wireless Networks:
- Use
airodump-ng wlan0monto scan for nearby Wi-Fi networks. This command will display a list of networks, including their BSSID (MAC address), channel, encryption type, and clients.
- Use
Targeting the Network:
- Select the target network and gather the following information:
- BSSID
- Channel
- Encryption type (WPA/WPA2)
- Run
airodump-ng -c <channel> --bssid <BSSID> -w <output_file> wlan0mon. Replace<channel>,<BSSID>, and<output_file>with the appropriate values. This command captures all the wireless traffic on that specific channel, saving it to a.capfile that you will need to analyze.
- Select the target network and gather the following information:
Capturing the Handshake (WPA/WPA2):
- For WPA/WPA2 networks, you need to capture the 4-way handshake.
- Use
aireplay-ng -0 10 -a <BSSID> -c <client_mac> wlan0monwhereis the MAC address of an active client. This deauthenticates the client, forcing it to reconnect and send the handshake. It can be challenging to find active clients. If this doesn't work, you can use aireplay-ng -3 -b <BSSID> -h <your_mac> wlan0mon.
Cracking the Password:
- Once you've captured the handshake (or if the network is WEP), you can start cracking the password.
- For WPA/WPA2: Use
aircrack-ng -w <wordlist> -b <BSSID> <output_file.cap>. The-woption specifies the location of your wordlist. - For WEP: Use
aircrack-ng -b <BSSID> -w <wordlist> <output_file.cap>or use theWEP crackingmethods in Kali Linux. - Be patient. Password cracking can take time, depending on the password complexity and the size of the wordlist.
Password Recovery:
- If the password is in the wordlist, Aircrack-ng will display it.
Advanced Techniques: Beyond the Basics
While the core steps provide a foundation, advanced techniques can significantly increase your chances of success.
Using RockYou.txt: This is one of the most popular wordlists. It contains millions of passwords, allowing you to crack a vast majority of passwords. Remember, that you may have to process this file before usage.
Creating Custom Wordlists: The creation of custom wordlists can significantly increase your chances of success when cracking a password.
Rainbow Tables: Pre-computed tables that can speed up password cracking, especially for WEP.
GPU Acceleration: Utilize your graphics processing unit (GPU) for faster password cracking, as it can handle the computational workload much more efficiently than the CPU.
Ethical Considerations: Responsibility and Legality
It is crucial to emphasize that attempting to access a Wi-Fi network without the owner's explicit permission is illegal and unethical.
Always Obtain Permission: Respect the privacy and security of others. Only attempt to crack networks that you own or have been authorized to test.
Know Your Local Laws: Laws regarding network access and security vary by location. Familiarize yourself with the relevant regulations in your jurisdiction.
Use Your Knowledge Responsibly: The techniques described in this guide are for educational and ethical purposes only. Use your skills to improve network security, not to cause harm.
Troubleshooting Common Issues
The Wi-Fi unlocking process isn't always straightforward, and you might encounter several issues. Here's how to troubleshoot some common problems:
Monitor Mode Not Working: Make sure your wireless adapter supports monitor mode and that the drivers are correctly installed.
No Handshake Captured: Ensure you are capturing the correct packets. Try deauthenticating connected clients or waiting for a client to connect.
Password Cracking Failing: Make sure you are using the correct wordlist, that the wordlist has relevant passwords, and that you have captured the handshake correctly.
Poor Signal Strength: Ensure you're close to the target network for optimal signal strength. Use directional antennas if necessary.
Conclusion: Reclaiming Digital Freedom
Unlocking Wi-Fi networks requires technical understanding, patience, and adherence to ethical guidelines. This guide provides the knowledge and tools to navigate the complexities of Wi-Fi security. Armed with this information, you can regain control over your digital life and leverage the power of wireless connectivity. Remember to prioritize ethical practices and use your skills responsibly.
